A suspected state-aligned threat actor has been attributed to a new set of attacks exploiting the Microsoft Office “Follina” vulnerability to target government entities in Europe and the U.S.
Enterprise security firm Proofpoint said it blocked attempts at exploiting the remote code execution flaw, which is being tracked CVE-2022-30190 (CVSS score: 7.8). No less than 1,000 phishing messages containing a lure document were sent to the targets.
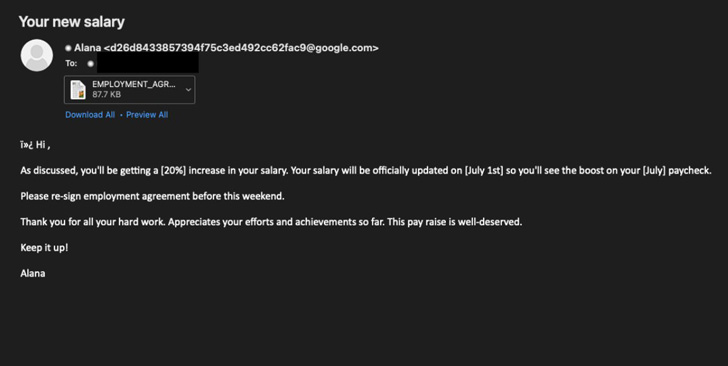
“This campaign masqueraded as a salary increase and utilized an RTF with the exploit payload downloaded from 45.76.53[.]253,” the company said in a series of tweets.
The payload, which manifests in the form of a PowerShell script, is Base64-encoded and functions as a downloader to retrieve a second PowerShell script from a remote server named “seller-notification[.]live.”
“This script checks for virtualization, steals information from local browsers, mail clients and file services, conducts machine recon and then zips it for exfil[tration] to 45.77.156[.]179,” the company added.
The phishing campaign has not been linked to a previously known group, but said it was mounted by a nation-state actor based on the specificity of the targeting and the PowerShell payload’s wide-ranging reconnaissance capabilities.
The development follows active exploitation attempts by a Chinese threat actor tracked as TA413 to deliver weaponized ZIP archives with malware-rigged Microsoft Word documents.
The Follina vulnerability, which leverages the “ms-msdt:” protocol URI scheme to remotely take control of target devices, remains unpatched, with Microsoft urging customers to disable the protocol to prevent the attack vector.
“Proofpoint continues to see targeted attacks leveraging CVE-2022-30190,” Sherrod DeGrippo, vice president of threat research, said in a statement shared with The Hacker News.
“The extensive reconnaissance conducted by the second PowerShell script demonstrates an actor interested in a large variety of software on a target’s computer. This, coupled with the tight targeting of European government and local U.S. governments led us to suspect this campaign has a state aligned nexus.”