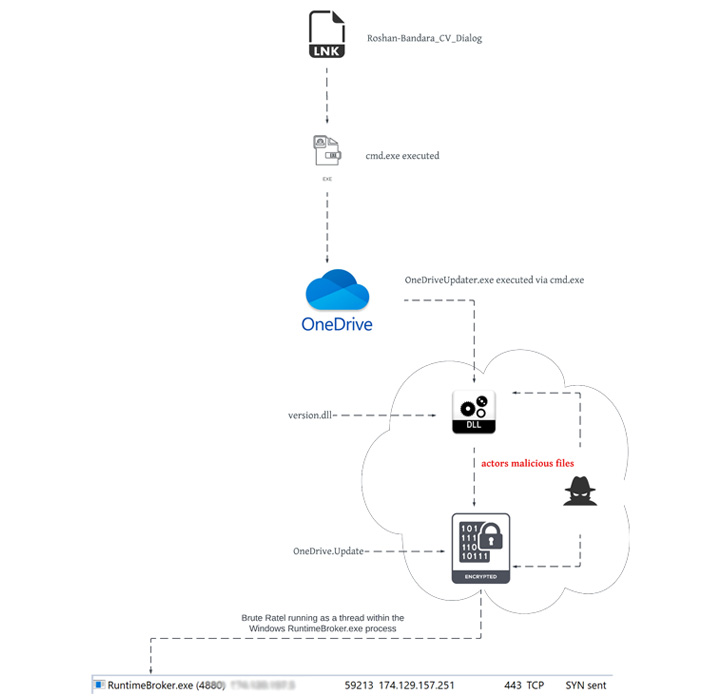
Malicious actors have been observed abusing legitimate adversary simulation software in their attacks in an attempt to stay under the radar and evade detection.
Palo Alto Networks Unit 42 said a malware sample uploaded to the VirusTotal database on May 19, 2022, contained a payload associated with Brute Ratel C4, a relatively new sophisticated toolkit “designed to avoid detection by endpoint detection and response (EDR) and antivirus (AV) capabilities.”
Authored by an Indian security researcher named Chetan Nayak, Brute Ratel (BRc4) is analogous to Cobalt Strike and is described as a “customized command-and-control center for red team and adversary simulation.”
The commercial software was first released in late 2020 and has since gained over 480 licenses across 350 customers. Each license is offered at $2,500 per user for a year, after which it can be renewed for the same duration at the cost of $2,250.
BRc4 is equipped with a wide variety of features, such as process injection, automating adversary TTPs, capturing screenshots, uploading and downloading files, support for multiple command-and-control channels, and the ability to keep memory artifacts concealed from anti-malware engines, among others.
The artifact, which was uploaded from Sri Lanka, masquerades as a curriculum vitae of an individual named Roshan Bandara (“Roshan_CV.iso”) but in reality is an optical disc image file that, when double-clicked, mounts it as a Windows drive containing a seemingly harmless Word document that, upon launching, installs BRc4 on the user’s machine and establishes communications with a remote server.
The delivery of packaged ISO files is typically sent via spear-phishing email campaigns, although it’s not clear if the same method was used to deliver the payload to the target environment.
“The composition of the ISO file, Roshan_CV.ISO, closely resembles that of other nation-state APT tradecraft,” Unit 42 researchers Mike Harbison and Peter Renals said, calling out similarities to that of a packaged ISO file previously attributed to Russian nation-state actor APT29 (aka Cozy Bear, The Dukes, or Iron Hemlock).
APT29 rose to notoriety last year after the state-sponsored group was blamed for orchestrating the large-scale SolarWinds supply chain attack.
The cybersecurity firm noted it also spotted a second sample that was uploaded to VirusTotal from Ukraine a day later and which exhibited code overlaps to that of a module responsible for loading BRc4 in memory. The investigation has since unearthed seven more BRc4 samples dating back to February 2021.
That’s not all. By examining the C2 server that was used as a covert channel, a number of potential victims have been identified. This includes an Argentinian organization, an IP television provider providing North and South American content, and a major textile manufacturer in Mexico.
“The emergence of a new penetration testing and adversary emulation capability is significant,” the researchers said. “Yet more alarming is the effectiveness of BRc4 at defeating modern defensive EDR and AV detection capabilities.”
Shortly after the findings became public, Nayak tweeted that “proper actions have been taken against the found licenses which were sold in the black market,” adding BRc4 v1.1 “will change every aspect of IoC found in the previous releases.”