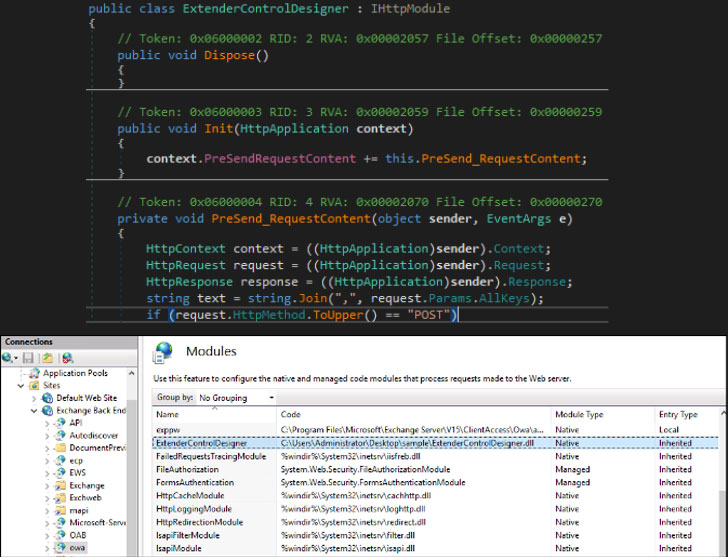
Malicious actors are deploying a previously undiscovered binary, an Internet Information Services (IIS) webserver module dubbed “Owowa,” on Microsoft Exchange Outlook Web Access servers with the goal of stealing credentials and enabling remote command execution.
“Owowa is a C#-developed .NET v4.0 assembly that is intended to be loaded as a module within an IIS web server that also exposes Exchange’s Outlook Web Access (OWA),” Kaspersky researchers Paul Rascagneres and Pierre Delcher said. “When loaded this way, Owowa will steal credentials that are entered by any user in the OWA login page, and will allow a remote operator to run commands on the underlying server.”
The idea that a rogue IIS module can be fashioned as a backdoor is not new. In August 2021, an exhaustive study of the IIS threat landscape by Slovak cybersecurity company ESET revealed as many as 14 malware families that were developed as native IIS modules in an attempt to intercept HTTP traffic and remotely commandeer the compromised computers.
As a persistent component on the compromised system, Owawa is engineered to capture the credentials of users who are successfully authenticated on the OWA authentication web page. Exploitation can then be achieved by sending “seemingly innocuous requests” to the exposed web services by entering specifically crafted commands within the username and password fields in the OWA authentication page of a compromised server.
Specifically, if the OWA username is “jFuLIXpzRdateYHoVwMlfc,” Owawa responds back with the encrypted credentials. If the username, on the other hand, is “dEUM3jZXaDiob8BrqSy2PQO1”, the PowerShell command typed in the OWA password field is executed, the results of which are sent back to the attacker.
The Russian security firm said it detected a cluster of targets with compromised servers located in Malaysia, Mongolia, Indonesia, and the Philippines that primarily belong to government organizations, with the exception of one server that’s attached to a government-owned transportation company. That said, additional organizations in Europe are believed to have been victimized by the actor as well.
Although no links have been unearthed between the Owowa operators and other publicly documented hacking groups, a username “S3crt” (read “secret”) that was found embedded in the source code of the identified samples has yielded additional malware executables that are likely the work of the same developer. Chief among them are a number of binaries designed to execute an embedded shellcode, load next-stage malware retrieved from a remote server, and trigger the execution of Cobalt Strike payloads.
Kaspersky’s Global Research and Analysis Team (GReAT) also said it identified an account with the same username on Keybase, where the individual has shared offensive tools such as Cobalt Strike and Core Impact, in addition to demonstrating an interest in the latter on RAIDForums.
“IIS modules are not a common format for backdoors, especially when compared to typical web application threats like web shells and can therefore easily be missed during standard file monitoring efforts,” Rascagneres and Delcher said. “The malicious module […] represents an effective option for attackers to gain a strong foothold in targeted networks by persisting inside an Exchange server.”