The U.S. Cybersecurity and Infrastructure Security Agency (CISA) is urging federal agencies to secure their systems against an actively exploited security vulnerability in Windows that could be abused to gain elevated permissions on affected hosts.
To that end, the agency has added CVE-2022-21882 (CVSS score: 7.0) to the Known Exploited Vulnerabilities Catalog, necessitating that Federal Civilian Executive Branch (FCEB) agencies patch all systems against this vulnerability by February 18, 2022.
“These types of vulnerabilities are a frequent attack vector for malicious cyber actors of all types and pose significant risk to the federal enterprise,” CISA said in an advisory published last week.
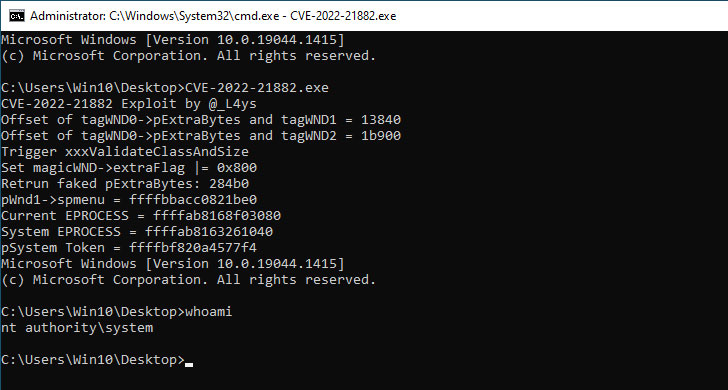
CVE-2022-21882, which has been tagged with an “Exploitation More Likely” exploitability index assessment, concerns a case of elevation of privilege vulnerability affecting the Win32k component. The bug was addressed by Microsoft as part of its January 2022 Patch Tuesday updates.
“A local, authenticated attacker could gain elevated local system or administrator privileges through a vulnerability in the Win32k.sys driver,” the Windows maker said. The flaw impacts Windows 10, Windows 11, Windows Server 2019, and Windows server 2022.
It’s worth noting that the security vulnerability is also a bypass for another escalation of privilege flaw in the same module (CVE-2021-1732, CVSS score: 7.8) that Microsoft resolved in February 2021 and has since been detected in exploits in the wild.