State-sponsored actors backed by the Russian government regularly targeted the networks of several U.S. cleared defense contractors (CDCs) to acquire proprietary documents and other confidential information pertaining to the country’s defense and intelligence programs and capabilities.
The sustained espionage campaign is said to have commenced at least two years ago from January 2020, according to a joint advisory published by the U.S. Federal Bureau of Investigation (FBI), National Security Agency (NSA), and Cybersecurity and Infrastructure Security Agency (CISA).
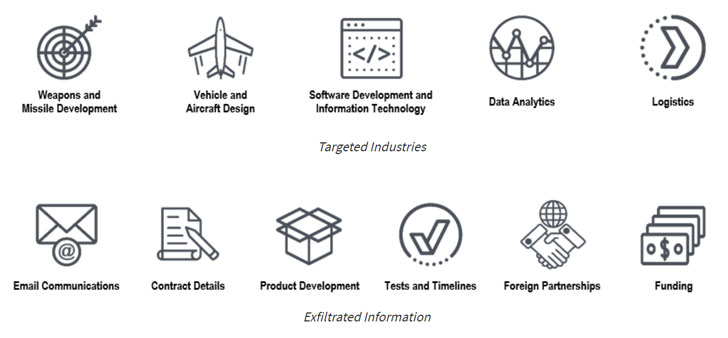
“These continued intrusions have enabled the actors to acquire sensitive, unclassified information, as well as CDC-proprietary and export-controlled technology,” the agencies said. “The acquired information provides significant insight into U.S. weapons platforms development and deployment timelines, vehicle specifications, and plans for communications infrastructure and information technology.”
Compromised entities include contractors that dabble in command, control, communications, and combat systems; surveillance and reconnaissance; weapons and missile development; vehicle and aircraft design; and software development, data analytics, and logistics.
The threat actors rely on “common but effective” tactics to breach target networks such as spear-phishing, credential harvesting, brute-force attacks, password spray techniques, and exploitation of known vulnerabilities in VPN devices, before moving laterally to establish persistence and exfiltrate data.
Some of the vulnerabilities leveraged by the attackers for initial access and privilege escalation are as follows –
- CVE-2018-13379 (CVSS score: 9.8) – Path traversal vulnerability in Fortinet’s FortiGate SSL VPN
- CVE-2020-0688 (CVSS score: 8.8) – Microsoft Exchange validation key remote code execution vulnerability
- CVE-2020-17144 (CVSS score: 8.4) – Microsoft Exchange remote code execution vulnerability
Many of the intrusions also involve gaining a foothold to enterprise and cloud networks, with the adversaries maintaining persistent access to the compromised Microsoft 365 environments for as long as six months to repeatedly harvest emails and data.
“As CDCs find and patch known vulnerabilities on their networks, the actors alter their tradecraft to seek new means of access,” the agencies explained. “This activity necessitates CDCs maintain constant vigilance for software vulnerabilities and out-of-date security configurations, especially in internet-facing systems.”
Among other malicious activities observed is the routine use of virtual private servers (VPSs) as an encrypted proxy and the use of legitimate credentials to exfiltrate emails from the victim’s enterprise email system. The advisory, however, does not single out any Russian state actor by name.
“Over the last several years, Russian state-sponsored cyber actors have been persistent in targeting U.S. cleared defense contractors to get at sensitive information,” said Rob Joyce, director of NSA Cybersecurity. “Armed with insights like these, we can better detect and defend important assets together.”