Attackers use rootkits to cover malware on a tool in a means that permits it to persist undetected over time, generally for years. Throughout that point, it could steal information or sources, or surveil communications. Working system-based rootkits are scary sufficient, however firmware rootkits much more so. Each search to persist, disguise and evade from processes and procedures to eradicate them.
Kernel or working system rootkits for a few years had been a harmful risk to computer systems. Then Microsoft made a serious change within the working system with Microsoft Vista in 2006. It required that distributors digitally signal drivers. This brought on not solely points with printer drivers, however extra importantly brought on malware writers to alter their assault strategies.
Kernel Patch Safety (KPP) required malware authors to beat a digital signing requirement. This meant that solely probably the most superior attackers used rootkits as a part of their payload. Rootkits went from being extremely used to solely being seen in underneath 1 p.c of the malware output for a few years.
Zacinlo advert fraud makes Home windows rootkits related once more
Then in June 2018, the Zacinlo advert fraud operation got here to mild and made us as soon as once more fear in regards to the threat of rootkits. As Bitdefender’s research identified, this rootkit-based malware has been in play for six years however solely not too long ago focused the Home windows 10 platform, with one key change: It used a digitally signed driver to bypass Home windows 10 protections. Researchers discovered that 90 p.c of the samples had been operating Home windows 10.
Rootkits, by definition, exit of their means to make sure that they persist when somebody runs primary cleansing strategies on an working system, and injecting the malware right into a signed Home windows 10 driver meant that’s precisely what the Zacinlo malware might do. Bitdefender lists these Zacinlo elements:
- A rootkit driver that protects itself in addition to its different elements. It will possibly cease processes deemed harmful to the performance of the adware whereas additionally defending the adware from being stopped or deleted.
- Man-in-the-browser capabilities that intercept and decrypt SSL communications. This enables the adware to inject customized JavaScript code into net pages visited by the person.
Zacinlo’s rootkit element is extremely configurable and shops all configuration information encrypted contained in the Home windows Registry, in line with Bitdefender. Throughout Home windows shut-down, the rootkit rewrites itself from reminiscence to disk underneath a distinct title and updates its registry key. That is the way it evades detection by regular antivirus methods.
Find out how to detect rootkit malware in Home windows 10
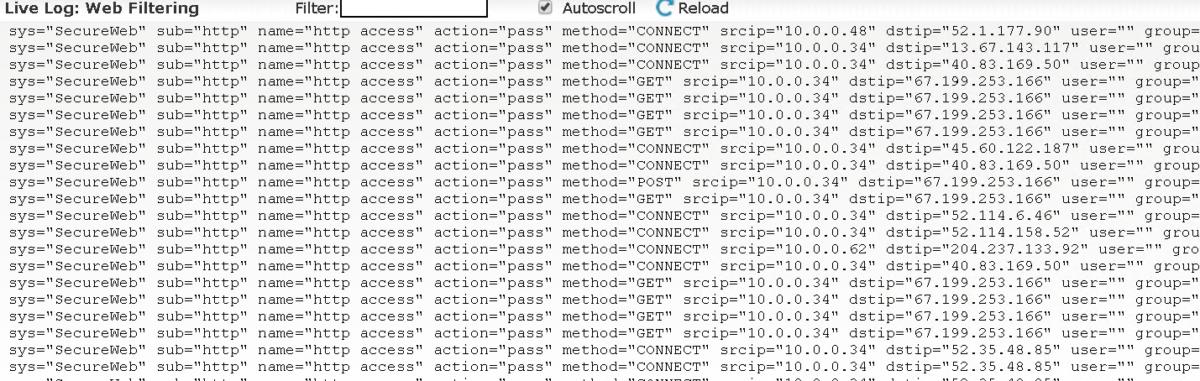
Usually one of the best ways to find out if a machine is contaminated by a rootkit is to evaluate outbound TCP/IP packets from a probably impacted machine. If in case you have a big community with a standalone egress filtering firewall, then you’ve gotten a key software at your disposal. That firewall will will let you see precisely what your workstations and community gadgets are connecting to as outbound packets in your community.
Your first purpose will probably be to evaluate the firewall’s reporting and see if will present what it’s good to see in case of assault. In the event you solely see IP addresses within the firewall logs, add person authentication information in order that monitoring is less complicated.
 Microsoft
MicrosoftEvaluation your present firewall logging reviews
Ideally, you’ve gotten a logging answer that alerts you to uncommon visitors or lets you block firewall visitors from geographic places. Because the attackers goal to be silent and never provide you with a warning to their actions, you might want to analyze implementing a proper log administration (LM) and security information and event management (SIEM) system. Firewall and occasion log information are sometimes rolled off the system shortly. To do forensic investigations or adjust to laws, you might must implement a storage mechanism for logging.
In a house or small enterprise setting, verify to see for those who can establish visitors within the firewall logs of your ISP’s modem, or your private firewall/router when you have such a tool. Export these log information right into a database parser program that may filter and type the visitors.
At a minimal, a system that’s misbehaving can typically be a key indicator {that a} rootkit is put in. Extreme CPU or web bandwidth utilization is commonly an indicator of an infection. Whereas a Home windows 10 machine could have extra web exercise than prior working programs with the necessity for packets being despatched to Home windows replace and telemetry, you must nonetheless be capable to decide when the machine just isn’t behaving usually.
In case your router doesn’t give you good recommendation as to what your programs are doing, it’s time to improve. Some private routers embrace subscription companies to scan for vulnerabilities and establish when gadgets try to contact different web addresses. Log in now to your router and evaluate what logging it has and if it may be adjusted and customised.
 Netgear
NetgearNetgear router with customization choices in logging
Find out how to forestall a rootkit malware assault
You have got some ways forestall rootkit malware from putting in in your programs. A method is to have stricter driver signing necessities. Windows S mode, in actual fact, permits solely trusted binaries issued by the Home windows retailer utility to be put in on the pc. Enabling Windows Defender Device Guard with a Home windows Enterprise license may even guarantee that you’ve additional safety.
Put processes in place to allow finish customers to inform the assistance desk or safety that they consider a rootkit is on their machine in order that applicable investigation might be undertaken. Usually a well-informed person is essential to find out if a machine has been contaminated. In case you are an IT admin, make sure that you practice your customers to identify and report rootkit signs.
Even primary security awareness training will assist forestall rootkits. The NIST guide to dealing with malware incidents on desktops and laptops lists the next IT insurance policies as key in defending programs. Customers shouldn’t:
- Open suspicious emails or e-mail attachments or click on on hyperlinks from unknown or identified senders, or go to web sites which can be more likely to comprise malicious content material
- Click on on suspicious net browser popup home windows
- Opening information with file extensions which can be more likely to be related to malware (e.g., .bat, .com, .exe, .pif or .vbs)
- Disable malware safety management mechanisms (e.g., antivirus software program, content material filtering software program, repute software program or private firewall)
- Use administrator-level accounts for normal host operation
- Obtain or execute purposes from untrusted sources
Find out how to take away rootkit malware
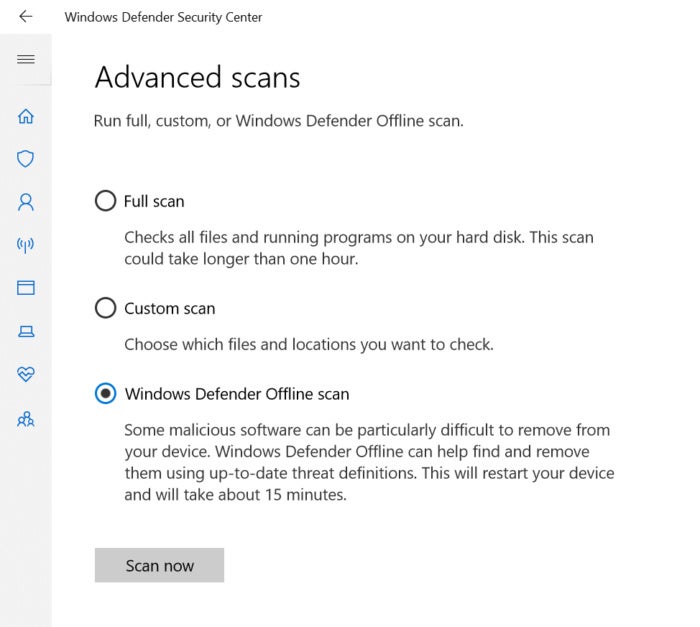
To scrub up rootkits, you’ve gotten a number of choices. You may run the Home windows Defender offline scan from inside Home windows 10. Go to the Home windows Defender Safety Middle, into Superior scans and verify the radius field to allow the Home windows Defender offline scan. When you reboot your system it can boot underneath the working system with a Home windows PE clear boot and scan the exhausting drive.
 Microsoft
MicrosoftHome windows Defender Offline scan
Extra instruments comparable to these from MalwareBytes and Kaspersky will carry out comparable duties. If a scan raises suspicion of a rootkit an infection, deal with it as a security incident. Take the suspected machine offline from the community and web instantly.
In case you are nonetheless uncertain in case your system has a rootkit, a number of useful boards can stroll you thru the method of research and detection. The BleepingComputer forums are a wonderful venue to help within the analysis of a system. One other useful venue for Home windows 10 computer systems is the TenForums site.
As soon as you identify your system is contaminated, completely rebuild the pc utilizing authentic software program. Alternatively, when you have a full backup, you possibly can roll the system again to earlier than the incident occurred and monitor the system for indicators of re-infection. As a part of the clean-up routine, reset the password to the system and alter the grasp password to your grasp password software program on the similar time.
Firmware rootkits require a distinct method
Rootkits embedded in a tool’s firmware might be tougher to recuperate from and clear up. Unified Extensible Firmware Interface (UEFI) rootkits are among the many scariest of this kind. In September 2018, APT28 was the primary UEFI rootkit discovered within the wild. The rootkit was embedded within the flash reminiscence of a tool’s Serial Peripheral Interface (SPI). That gave the rootkit persistence in opposition to each reinstallation of the working system and alternative of the exhausting drive.
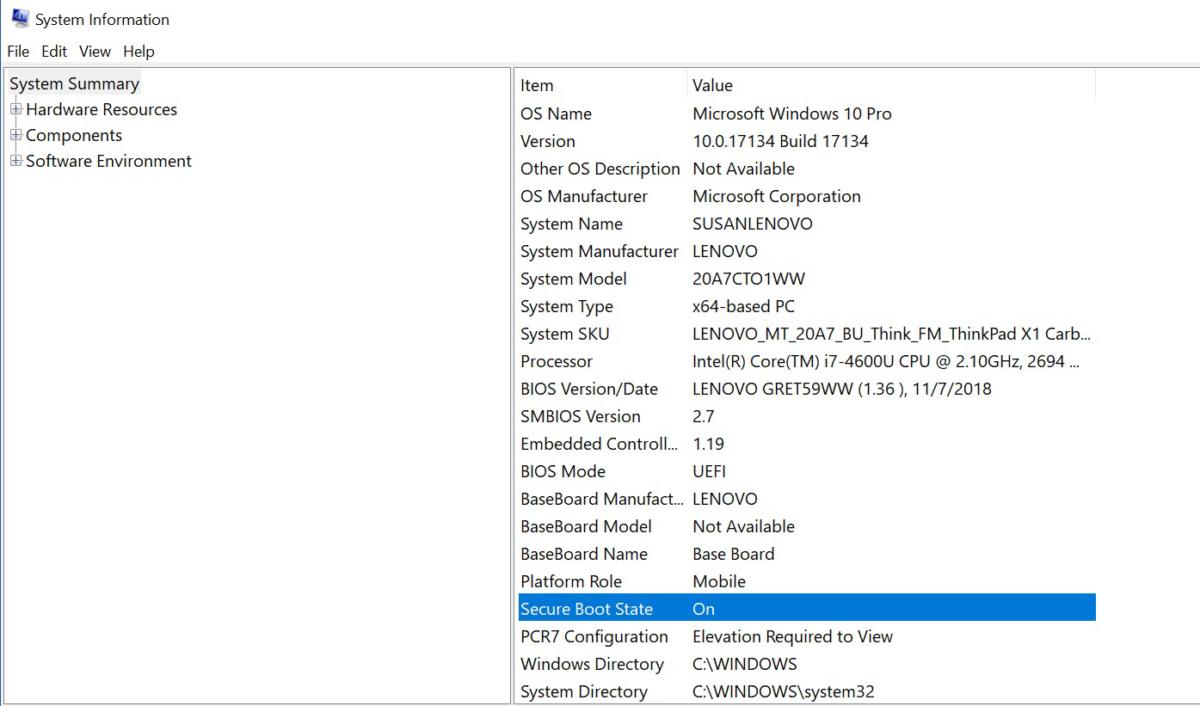
To guard your self from BIOS, UEFI or different firmware rootkits, make sure that your programs’ firmware is updated. Verify to see in case your system is using secure boot. Safe boot has been round for many years and is designed to guard the preboot system by making certain solely trusted code might be run throughout this course of. To find out in case your Home windows 10 system is presently operating in safe boot state, open your Begin menu and kind “System Info”. Within the ensuing window, scroll down and search for the Safe boot state. If it lists that it’s on, then your system is already operating on this protected mode.
 Microsoft
MicrosoftDecide your Safe boot state
GITHUB lists many sources that will help you decide in case your firmware is present. Make updating system BIOS and firmware a part of your pc safety course of. In the event you would not have a software from the {hardware} vendor to mechanically verify and set up bios updates, you might want to set up one. HP, for instance, has a HP support assistant software.
Do not forget that rootkits aren’t only for Home windows gadgets. They are often launched into web of issues (IoT) gadgets as nicely. In the event you suspect a tool has been was a malicious machine, reset it to manufacturing facility defaults, then guarantee it’s updated on its firmware. Final however not least, reset the password related to the username or account with the machine.
In case you are impacted by a rootkit, one of the best ways to recuperate is to totally reinstall the working system and set up or reinstall firmware. Reset passwords to accounts as wanted. Prevention is clearly simpler than the treatment, however you possibly can recuperate so long as you make sure that you’ve gotten the power to reinstall the working system and purposes.
Begin now by downloading and storing a clean Windows 10 ISO on a flash drive, and be sure to have key purposes and set up codes both backed up or saved at offsite places that may be accessed ought to an infection happen.

