Continuing with the ongoing wave of phishing campaigns, another attack surfaced online. This one abuses Amazon AWS services to trick users. This phishing attack fools users by sending a fake AWS account suspension email.
False AWS Account Suspension Emails
According to BleepingComputer’s Lawrence Abrams, a new phishing campaign has surfaced online where the scammers abuse Amazon. Specifically, the attackers behind this phishing attack send fake emails to the users alerting them about Amazon AWS account suspension. Though, these emails are never true.
As elaborated in a blog post, the attack begins by sending fake emails alerting users about the suspension of Amazon AWS accounts for unpaid bills. The subject line of the email suffices to panic the recipient.
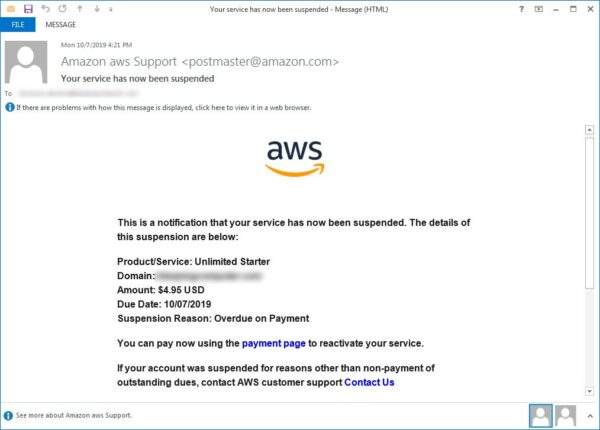
The email message includes an embedded URL where the recipient should supposedly click to pay the overdue bills. When clicked, the link redirects the user to the phishing web page impersonating the Amazon AWS login page. The URL of this web page bears a fake domain. However, the start of the URL contains “aws.amazon.com” – enough to confuse the user especially when he or she is viewing the page on a mobile phone. Though, someone visiting this web page on a PC browser can view the entire URL to detect the deception fairly easily.
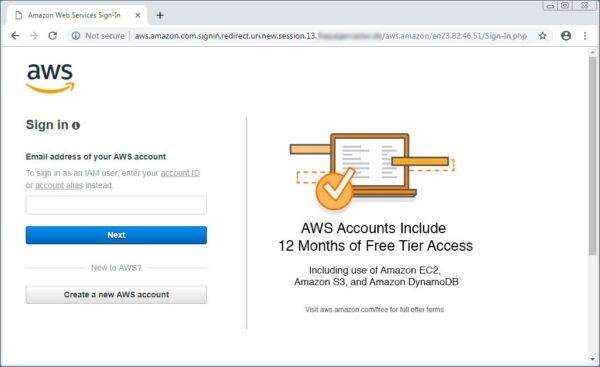
As evident, the page requires the user to enter their login credentials which will eventually fall into the hands of the attackers.
In the end, the attackers tend to veil their attack by redirecting the victim to the genuine AWS login page after entering the credentials.
Be Wary Of Spoofing
While this campaign looks like any other email phishing attack, what makes this one more dangerous is the spoofed email address. The sender’s email address spoofs the legitimate Amazon Support account “[email protected]”. Hence, the recipients of phishing emails are more likely to believe the message.
By exploiting different open relay vulnerabilities the attackers can easily spoof the ‘From’ email address.
Therefore, the key to fend off such attacks involving a spoofed email address is to thoroughly review the embedded URLs. Lawrence Abrams recommended the following:
Even if a phishing email looks legitimate, it is important to pay attention to the URLs of the landing pages before entering your login credentials in a displayed login form. If you are on mobile, you can press on the link until the full URL is displayed to make sure it’s not a fake landing site.
Let us know your thoughts in the comments.

