While VPNs provide privacy to users, they can also threaten users security from security bugs. Recently, a unit of UK spy agency GCHQ has issued alerts for users of various VPN brands for vulnerabilities. The VPNs from Pulse secure, Fortinet, and Palo Alto have these bugs under active exploitation.
UK Spy Agency Alerts Of VPN Vulnerabilities
The National Cyber Security Centre (NCSC) has issued a warning for users of numerous VPNs. NCSC, which is a unit of UK’s spy agency Government Communications Headquarters (GCHQ), alerts the users for multiple VPN vulnerabilities exploited in the wild.
According to their advisory, these vulnerabilities allowed an attacker to retrieve arbitrary files and steal VPN’s login credentials. An attacker could then abuse the credentials to make changes in VPN configuration settings or gain access to internal infrastructure. The attacker could also run secondary exploits to access a root shell by exploiting these bugs.
While NCSC noticed numerous bugs under exploit, they highlighted six of these having the most impact. Two of the bugs existed in Pulse Connect Secure, three in Fortinet, and one in Palo Alto.
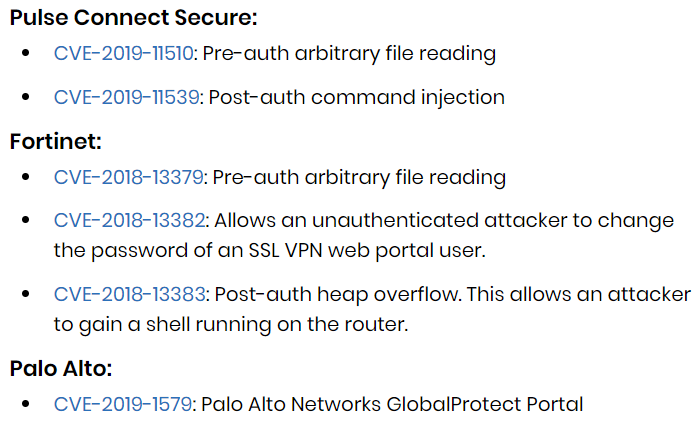
Patches Rolled Out – Update Now!
Since all three vendors have released fixes for the vulnerabilities, NCSC recommends users of these VPNs to update their systems at their earliest convenience. They also suggest users check logs for possible compromise.
Users of these VPN products should investigate their logs for evidence of compromise, especially if it is possible that patches were not applied immediately after their release.
Moreover, admins should also check for compromised accounts under active use. In addition, NCSC also advises all users to reset their VPN accounts credentials as possible mitigation.
For organizations which detected exploitation of their VPNs, NCSC recommends them to keep a check on all configuration settings for any unauthorized changes, monitor logs, enable two-factor authentication, and disable any functionality or ports not in use. Whereas, for devices suffering successful exploitation where they cannot detect the changes, the admins should factory reset the device.
Let us know your thoughts in the comments.

