Once again, a new banking Trojan variant has surfaced online that draws attention owing to its typical features. Termed ‘Ginp’, the malware specifically poses a threat to Android devices and is likely to surpass other banking trojans soon.
About Ginp Malware Targeting Android
Researchers from ThreatFabric have shed light on a new banking malware strain. This time, they have delved into the details of the ‘Ginp’ Android banking Trojan, already active in the wild.
According to the researchers, Ginp surfaced online earlier this year and has been active for at least 5 months. Since June 2019, this malware has exhibited frequent updates to its codebase. Though, the authors of this malware seemingly copied the code of Anubis Trojan for core functionalities.
This malware surfaced on the Play Store for the first time in June 2019 as the ‘Google Play Verificator’ app. At that time, it specifically aimed at stealing SMS messages.
Later, in August 2019, it masqueraded as ‘Adobe Flash Player’ apps bearing numerous malicious features. The malware could perform overlay attacks and abuse Accessibility Service to become the default SMS app.
After that it reappeared in two different versions, targeting social media apps, and then banking apps, respectively, each bearing enhanced features.
Finally, in November, the final version (for now) surfaced online with an added functionality of achieving device admin permission.
While the technical details are available in the researchers’ blog post, here, we quickly review how this malware works.
Upon reaching the target device masquerading as a legit app, the malware hides the app icon. Then, it asks Accessibility Service permissions from the user.
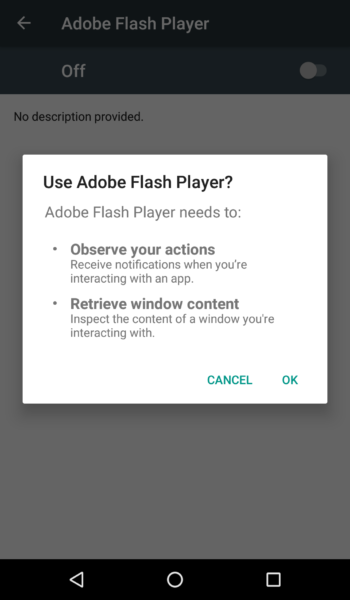
Once granted, it then attains dynamic permissions automatically to send messages and make calls without user input. It can then perform overlay attacks.
Similarities With Anubis
The analysis of Ginp malware revealed striking similarities with the infamous Anubis Trojan to the researchers.
Nonetheless, it isn’t exactly a reminiscence of Anubis, rather an inspiration that reuses some of the Anubis’ code.
Likewise, it exhibits similar names for Android components.

Presently, the malware seems focused on Spanish banks as it masks itself as seemingly legit banking apps.
All the targeted apps relate to Spanish banks, including targets never seen before in any other Android banking Trojan. The 24 target apps belong to 7 different Spanish banks: Caixa bank, Bankinter, Bankia, BBVA, EVO Banco, Kutxabank and Santander.
The researchers suspect that the malware may exhibit a further increase in its malicious features and targets as well.
Earlier, ThreatFabric also highlighted another banking Trojan ‘Cerberus’ targeting Android devices. It was also a robust malware bearing various malicious features.

