Microsoft users once again face threats from a new phishing attack. This time, the attackers have utilized a new strategy to bluff users and steal their login credentials.
Microsoft Phishing By Local Login Forms
Reportedly, ISC handler Jan Kopriva noticed a new phishing attack targeting Microsoft account users. While there is nothing seemingly new with this campaign with regard to the motives of the phishing attack, however the technique with which it executes the attack is unique.
As elaborated in a post, Kopriva noticed an email notifying users about a ‘copy of payment notification’. The email had very short text, the researcher also noticed it had a HTML attachment too.
Unlike most HTML code in phishing attacks that redirect users to phishing websites, the one in this attack behaved differently. Opening the attachment displayed a login page as a pop-up.
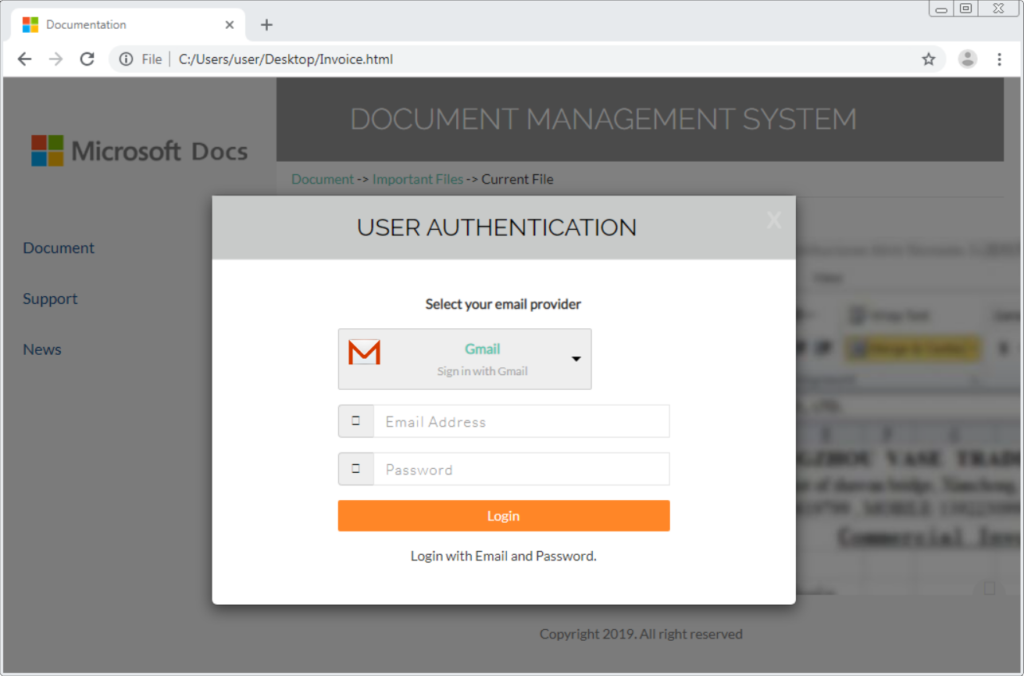
This page resembled the Microsoft website and did offer numerous options for users to choose the right email provider. Perhaps, this was a technique to target even non-Microsoft users.

The victim can choose an option from this window to sign-in. As soon as the victim enters their username and password, the screen shows an attempt to connect to the mail server.
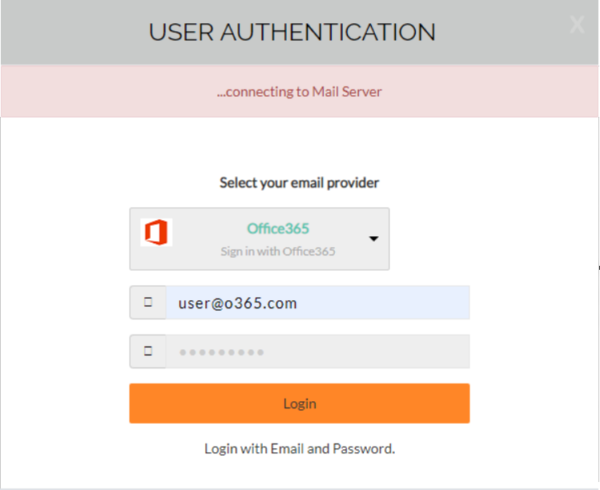
Whereas, in the background, it transfers the credentials via HTTP GET request to a remote server.
It then also asks for the victim’s phone number and recovery email which it transfers to the server via HTTP POST.
The user then lands on another page showing a fake invoice, which then further redirects to end the attack. As explained by the researcher,
The browser is redirected to a low-quality picture of the supposed invoice (at least I assume…) and after a couple of seconds redirected again, this time to either a legitimate Microsoft site or to the domain specified in the recovery e-mail supplied by the user.

An Unusual Phishing Trick
Though, the aim of this phishing attack looks similar to the usual phishing campaigns, i.e., stealing credentials. However, the technique it uses seems unique.
At first, the researcher found its unusual code, regarding which, he states,
When I opened the 930 kB long file in a text editor, the only text visible at first glance was on the first line:
After it, there were 4735 empty lines followed by a lot of obfuscated JavaScript along with several legitimate and only Base64-encoded JavaScript libraries (e.g. jQuery, Bootstrap,…).
Owing to its length of over 600K characters, it was not possible to manually deobfuscate and analyze the code. So, the researcher checked via alternative means.
After opening the file in Chrome in a VM, it became obvious why the script was so large. Unlike most other HTML-based phishing attachments, this one didn’t depend on an external fake login page, but carried the entire thing inside its body.
The researcher suspects that with this technique, the attackers possibly attempt to bypass the security mechanisms. Nonetheless, he has clearly called this technique of adding HTML attachments “anything but usual”.
This was the first time I came across such a complex HTML phishing attachment, i.e. one, that carried all the libraries and files in one package and didn’t depend on a remote server for anything else than for collecting the stolen credentials.
As always, users should remain cautious while clicking on emails from untrusted or unknown sources and opening attachments.
Let us know your thoughts in the comments.

