Heads up Spotify users! A new phishing attack is in the wild that lures Spotify users into revealing their banking details. Fortunately, identifying the legitimacy of the email isn’t too difficult for a savvy user.
Spotify Phishing Attack Aimed At Stealing Card Details
The Australian email security firm MailGuard recently warned users of a new Spotify phishing campaign in the wild. This phishing attack aims at Spotify users in an attempt to steal their payment card data.
As elaborated in the blog post, the attackers behind this campaign have made every effort to design legit-looking emails. From the subject line to the contents of the email and the phishing web pages in which they have attempted to impersonate the original Spotify layout.
The attack begins from the fake email reaching the users’ inbox with the subject “Your payment didn’t go through”. Opening the email then shows a message to the user regarding a failed payment for their Spotify account.
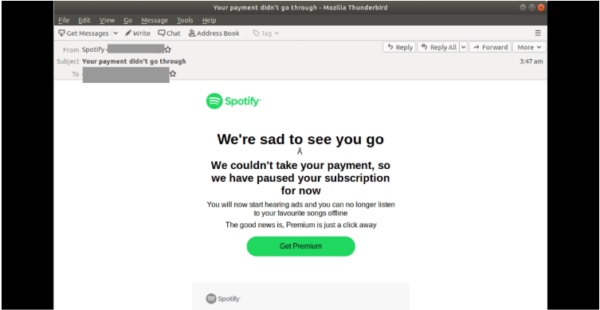
Once a user clicks on ‘Get Premium’, he or she lands on the first phishing web page. Here, the user has to sign-in to the Spotify account. Entering the credentials here allows the attacker access to the victims account login details.
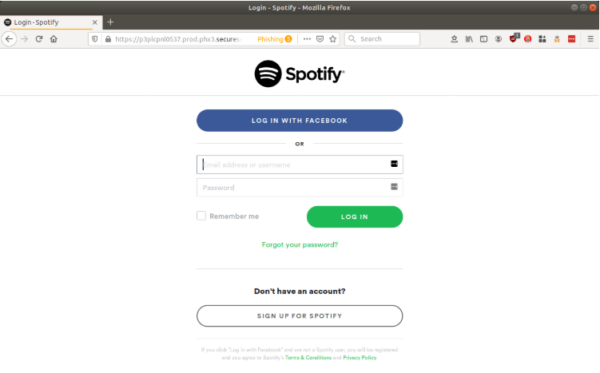
Clicking on the ‘Log In’ button then takes the victim to the next page asking payment card data.
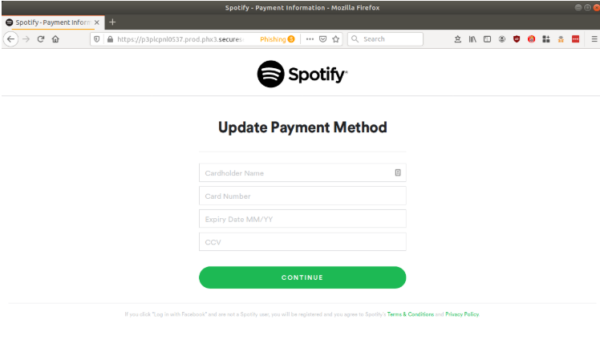
Then, upon clicking on the ‘Continue’ button, the victim lands on the last web page of this phishing attack which asks the victim to enter their billing address.
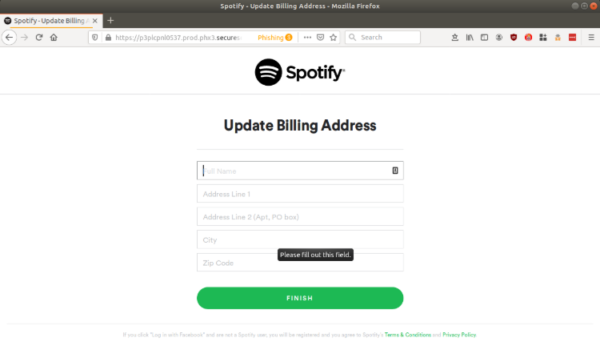
Clicking on the ‘Finish’ button lands the victim to a non-existent page showing 404 not found error, thereby ending the attack. As always, the victim ends up losing important details to the hacker.
Avoid Phishing By Keenly Observing Your Emails
Despite all the efforts from the attackers to create near-original emails, their still remains a few loopholes. Observing these differences can allow a savvy user to identify the deception.
At first, the sender’s email address isn’t a legit one. A quick look at the complete sender’s address would reveal the fake web link.
Similarly, there are numerous formatting errors in the email body that help to indicate the falsehood of the message.
Let us know your thoughts in the comments.

