The year 2021 was eventful in terms of digital threats for organizations and individuals, and financial institutions were no exception. Throughout the past year, we have seen cybercriminals continue to actively target our users with tools and techniques that emerged due to the pandemic. Imperfections in the transition to remote/hybrid work continue to pose a huge threat to businesses. On top of that, economic issues caused by the pandemic have only aggravated the problem. Driven by poverty and unemployment, cybercriminals intensified their malicious activity against bank customers and bank infrastructure.
Well-known financial threats remain prominent. SpyEye, developed in 2009 and described as a “bank Trojan with a form grabbing capability”, surged from the eighth most common banking malware tool with a 3.4% share in 2020 to the second most common in 2021 with 12.2%. Emotet (9.3%), described by Europol as “the world’s most dangerous malware”, underwent a drop of five percentage points between 2020 and 2021.This is linked to the fact that law enforcement agencies around the world worked together to obstruct the botnet’s infrastructure at the beginning of 2021, so its activities were disrupted for at least part of that year.
While 2021 did see an increase in threats to financial institutions on a global scale, it also saw PC and mobile malware continue on the downward trend previously seen in 2020. The mass change in cybercriminals’ objectives and methods seen in 2020 continued in 2021. Cybercriminals have found ways to benefit from the changes brought by the pandemic, adapting their goals and methods to take advantage of the shifts to teleworking and online shopping. This report aims to offer thorough insights into the financial cyberthreat landscape in 2021.
The research in this report is a continuation of our previous annual financial threat reports (2018, 2019 and 2020), providing an overview of the latest trends and key events across the threat landscape. We look at phishing threats commonly encountered by users and companies as well as the prevalence of various Windows and Android-based financial malware.
Methodology
For the purposes of this report, “financial malware” refers to malicious software targeting entities within the financial services sector, including online banking, payment systems, e-money services, online stores and cryptocurrency services. The term is also used to describe malware seeking access to financial organizations’ IT infrastructures.
Besides financial malware, we analyzed phishing activities, notably the design and distribution of financially themed web pages and emails intended to impersonate well-known legitimate sites and organizations in order to deceive prospective victims into providing their private information to be exploited by the cyberattackers.
To examine the financial threat landscape, we have analyzed the malicious activities on devices owned by individuals running Kaspersky security products, which they volunteered to make available to us through Kaspersky Security Network. Maliicious activities on devices with Kaspersky products were assessed along with corporate user statistics, which were also collected from customers who agreed to share data from their enterprise security solutions. All statistics from Kaspersky Security Network are anonymized.
Data from 2021 was compared to data from 2020 to assess year-on-year trends in malware development. However, for the sake of further insight into evolutionary trends in financial malware, occasional references to preceding years are also included.
Key findings
Phishing:
- In 2021, 8.2% of users were hit by phishing
- E-commerce-related phishing continued to exceed banking-related phishing, as it did in 2020, making up 17.6% of all phishing schemes in 2021, compared to the 11.1% share for banking
- PayPal users maintained their position as the most frequently targeted payment system users, with phishing pages mimicking this payment system accounting for 37.8% of such attacks in 2021. Visa, formerly a longtime leader in the category, retained its fourth place with a 9.4% share
PC malware:
- In 2021, the number of users attacked by banking Trojans continued to decline from 625,364 in 2020 to 405,985 in 2021 – a 35% drop
- The countries with the largest numbers of targeted users in 2021 were Turkmenistan, Afghanistan and Tajikistan
- Zbot (20.5%) remained the most prevalent banking malware, followed by SpyEye (12.2%), which saw a notable jump in presence, and CliptoShuffler (10.2%)
- Corporate threats from banking malware grew by almost two percentage points to 37.8%, with the remaining 62.2% representing consumer banking malware attacks
Mobile malware:
- In 2021, the number of Android users attacked by banking malware saw another precipitous drop, with numbers falling from 294,158 in 2020 to 147,316 in 2021 – a 50% drop
- Among countries and territories around the world, we observed the highest percentage of Android users targeted by banking malware in Japan, Spain and Turkey. Turkey replaced Taiwan in the top three, with the latter completely falling off the top ten list
Financial Phishing
Phishing is one of the most prevalent forms of cybercrime due to minimal effort required and the fact that it really works. It’s usually built around an inherently simple scheme: using carefully crafted emails or notifications that mimic messages from banks, government organizations, entertainment platforms – really any service – cybercriminals can trick users into following a link to a fraudulent website and giving up their payment or personal details or even downloading malicious programs.
In 2021, Kaspersky anti-phishing technologies detected over 250 million attempts to follow a phishing link on user computers, with 8.2% of users encountering an attack. As many as 41.8% of those attacks were related to financial phishing.
Percentage of financial phishing attacks (of the overall phishing attacks) detected by Kaspersky, 2016 – 2021 (download)
In this case, “financial phishing” refers not only to banking specific phishing but also payment systems and e-shops. Payment system phishing includes pages impersonating well-known payment brands, such as PayPal, MasterCard, American Express, Visa and others. E-shops refer to online stores and auction sites like Amazon, the Apple Store, Steam, eBay etc.
In 2021, phishing cases detected by Kaspersky showed that e-shop phishing was the most common, representing 17.6% of all phishing and over 40% of financial phishing. We attribute the significant size of these figures to the impact of the pandemic on users’ technology habits, with many starting to do more shopping online, increasing the potential supply of targets for cybercriminals.
Payment systems were the target of about one-third of all financial phishing and banks made up the rest at 26.6%, accounting for 11.1% of all phishing cases.
Distribution of financial phishing cases by type in 2021 (download)
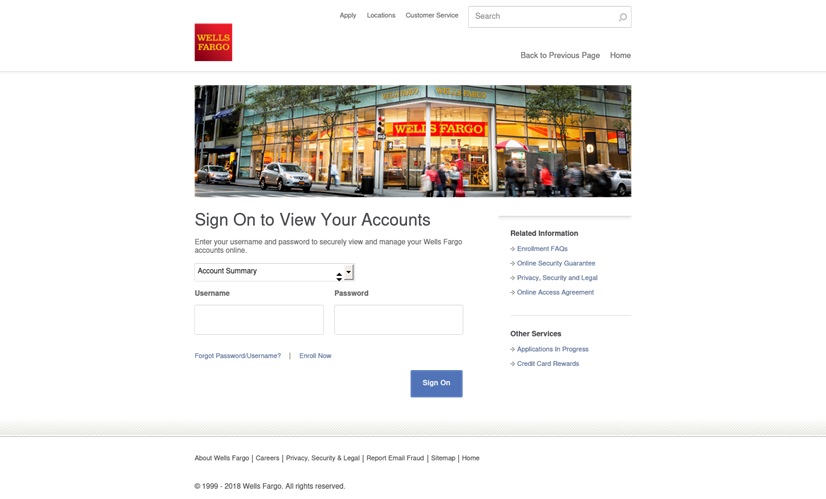
The bank-related phishing example below showcases the similarity of fake pages to the authentic companies they are impersonating. Phishers use the bank’s logo and a photo of its office. Victims would mistake it for a real bank page and unknowingly relay all information needed to access their accounts.
A phishing login and account verification page imitating a U.S. financial services company, Wells Fargo
Payment system brands most frequently used in financial phishing schemes, 2021 (download)
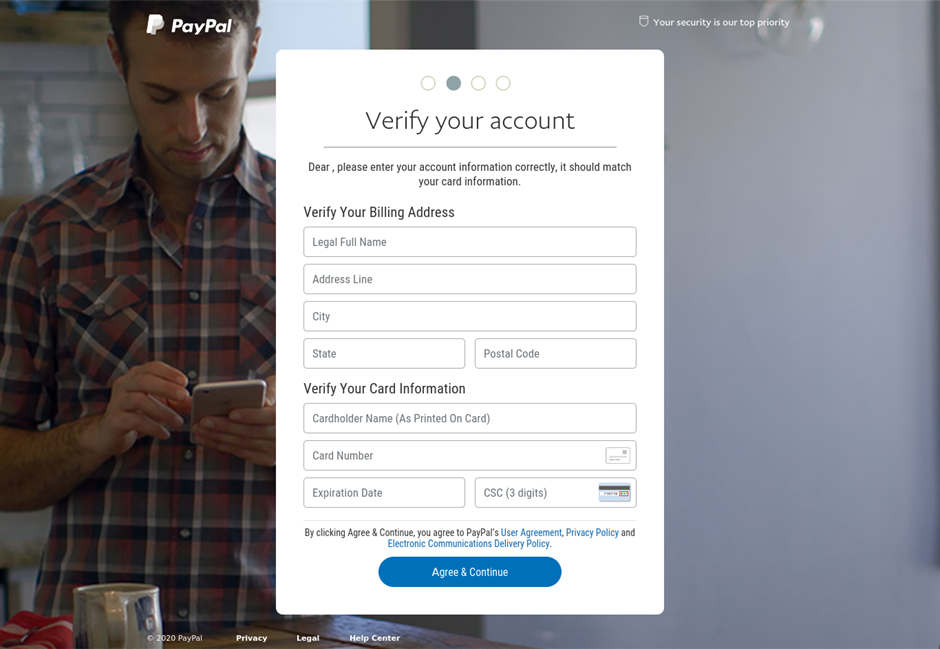
As the graph above shows, PayPal was by far the most commonly used payment system in phishing attacks, making up 37.8% in 2021.
This example of a phishing page aimed at PayPal users directly asks prospective victims to include their payment details
Meanwhile, Mastercard held second-place in the attacked payment systems ranking at 12.2%. American Express phishing scams also have held consistent over the years with 10% in 2021.
E-shop brands most frequently used in financial phishing schemes, 2021 (download)
Throughout the past year, scammers extensively targeted users of various retail platforms. In 2021, Apple was the most used brand for phishing schemes at 48.78%. Amazon held second place with 21.48%. Meanwhile, eBay noticeably took only 5.32% in 2021. Alibaba, a Chinese multinational tech company, is also in the top four attacked online stores of 2021. The company’s users were the target of 4.14% of phishing schemes.
An example of a phishing login page targeting Amazon customers around the world
A noticeable development was the prominence of cryptocurrency-related phishing scams. In 2021, there were over 460,000 crypto-related phishing attempts. This could potentially be explained by the growing trend and legitimization of NFTs and cryptocurrencies, as well as cryptocurrency prices, which soared at the end of 2020 and stayed high throughout 2021.
An example of a phishing page targeting investors and borrowers of various cryptocurrencies
Cryptocurrency-related phishing schemes are likely to grow as this newer digital payment system continues to gain popularity, because with increased uptake comes more potential victims to cybercriminal activities. However, cryptocurrency prices are not to be underestimated: if Bitcoin drops in 2022, the overall interest in cryptocurrency may also drop. In February 2022, we observe it starting growing again, though.
Banking malware for PC
This study analyses the banking malware used to steal credentials needed to access victims’ online banking or payment systems accounts and to intercept one-time passwords for two-factor authentication.
Our findings showed that in 2021, the number of users attacked by banking malware continued to decline, going from 625,364 in 2020 to 405,985 in 2021 – a 35% drop. This follows an increasingly downhill trend, with this figure dropping 20% between 2019 and 2020, and a near 13% between 2018 and 2019.
This trend is attributed to the increasingly targeted nature of attacks, as cybercriminals pivot to prioritizing large business targets. Nevertheless, individuals and small businesses remain a large proportion of those victimized by cybercriminal groups like Zbot, SpyEye, CliptoShuffler and Emotet, among others.
Dynamic change in the number of unique users attacked by banking malware in 2019 – 2021 (download)
The main actors among banking malware
Every year, we detect multiple families of banking malware – groups of applications with similar attack techniques and the same code base. The lifecycle of these malware families varies, some become obsolete and others only expand.
TOP 10 PC banking malware families, 2021 (download)
Our tracking of the banking malware families showed that about half of all affected users were attacked only by four families. Zbot maintained its position as the most popular malware with financial cybercriminals, making up one-fifth of all attacks. SpyEye made a notable jump from number eight on the list to number two, going from 3.4% in 2020 to 12.2% in 2021. Gozi and Nuerevt fell out of the top ten, the former of which accounted for one=fifth of all financial malware attacks in 2018. They were replaced by Cridex and Nymaim.
Geography of attacked users
For this report, we calculated the percentage of Kaspersky users in each country that encountered a threat out of the total number of Kaspersky users in the country in order to ascertain the risk of computer infection in different countries around the world. Note that in previous reports, we used a different methodology. For this reason, numbers for the year 2020 in this section will also be different.
TOP 20 countries with the greatest share of attacked users are presented in the table below. More than half of all infection attempts occurred in these 20 countries.
| Country* | Share of attacked users |
| Turkmenistan | 8,3% |
| Afghanistan | 6,4% |
| Tajikistan | 6,4% |
| Uzbekistan | 5,3% |
| Yemen | 3,1% |
| Paraguay | 2,6% |
| Sudan | 2,4% |
| Kazakhstan | 2,1% |
| Syria | 2,1% |
| Zimbabwe | 2% |
| Lithuania | 1,8% |
| China | 1,7% |
| Venezuela | 1,7% |
| Costa Rica | 1,6% |
| Pakistan | 1,5% |
| Kyrgyzstan | 1,5% |
| Iran | 1,4% |
| Belarus | 1,4% |
| Cameroon | 1,3% |
| Egypt | 1,2% |
*Countries with less than 10 000 Kaspersky users are excluded from these statistics
Turkmenistan (8.3%) was the most attacked country by banking malware for PC. Afghanistan (6.4%) and Tajikistan (6.4%) share second and third place, respectively. Uzbekistan (5.3%), which was the leader in 2020, now landed fourth, losing 3.5 p.p., and Yemen (3.1%) climbed to the fifth position.
The shares of Paraguay (2.6%) and Sudan (2.4%) grew slightly, while Kazakhstan (2.1%) and Syria (2.1%) lost around 1 p.p. and shared eighth and ninth places. Zimbabwe (2%) rounds out the TOP 10, and Lithuania (1.8%) added 1 p.p. and climbed to eleventh position.
Types of users attacked
Our research has confirmed our hypothesis that financial malware is becoming increasingly corporate rather than consumer focused. Between 2020 and 2021, corporate users’ share of banking malware targets increased by almost 2 percentage points and grew by a noticeable 13.7 percentage points between 2018 and 2021. However, in recent years, the growth of corporate user share has been noticeably slower than in the pre-pandemic years, and attacks against consumers still outweigh corporate threats with the former making up 62.2% of financial malware attacks in 2021 and the latter, 37.8%.
PC malware attack distribution by type (corporate vs consumer), 2020–2021 (download)
We attribute this to the continuing shift towards a remote and hybrid modes of work. Though the pandemic saw a rise and fall in the number of restrictions, many companies decided not to come back to the familiar office work mode. Meanwhile in some organizations, employees had to resort to using home devices protected by consumer solutions for working purposes. If these users receive a malicious message both by personal and corporate email, the detection will count as consumer targeting. That means that cybercriminals may be even more interested in corporate users than our statistics show.
Mobile banking malware
Kaspersky experts have been analyzing Android banking malware for years and have observed an interesting steep downward trend.
In 2019, the number of Android users attacked by banking malware dropped from 1.8 million in 2018 to a little over 675,000. Then in 2020, the figure dropped an additional 55% to 294,158. This year we saw a similar drop of almost 50%, making the total number of Android users attacked with banking malware in 2021 147,316.
Number of Android users attacked by banking malware by month, 2021 (download)
To understand these trends, we assessed the impact and changes of the most prevalent mobile malware.
The year 2021 saw Agent supplant Asacub as the number-one mobile malware, representing 26.9% of attacks. Asacub (18.8%) dropped from its number one placement in 2019 and 2020 to third in 2021, dropping 6.8% percentage points since 2020. Svpeng (21.4%), which seeks administrator rights on infected devices, grew by almost nine percentage points between 2020 and 2021, thus reclaiming its position in the TOP 3, and surpassing Asacub.
In 2020, Rotexy (1.6%), which has capabilities of both a banking Trojan and a ransomware locker, was the third most common type of Android banking malware with a 17.9% share. However, in 2021, Rotexy dropped by 16.3 percentage points to tenth place.
TOP 10 Android banking malware families, 2021 (download)
Geography of attacked users
TOP 10 countries and regions by percentage of Android users targeted by banking malware in 2020.
| Country/region | Share of users* |
| Japan | 2,83% |
| Taiwan | 0,87% |
| Spain | 0,77% |
| Italy | 0,71% |
| Turkey | 0,60% |
| Korea | 0,34% |
| Russian Federation | 0,25% |
| Tajikistan | 0,21% |
| Poland | 0,17% |
| Australia | 0,15% |
* Number of users encountering mobile banking malware as a percentage of the total number of users of Kaspersky mobile solutions in the country or region
TOP 10 countries and regions by percentage of Android users targeted by banking malware in 2021.
| Country/region | Share of users* |
| Japan | 2,18% |
| Spain | 1,55% |
| Turkey | 0,71% |
| France | 0,57% |
| Australia | 0,48% |
| Germany | 0,46% |
| Norway | 0,31% |
| Italy | 0,29% |
| Croatia | 0,28% |
| Austria | 0,28% |
* Number of users encountering mobile banking malware as a percentage of the total number of users of Kaspersky mobile solutions in the country or region
Interestingly, Japan (2.18%), which did not make the top ten in 2019, was once again the number one country in 2021 after rising to the top position in 2020. Russia went from being in the top position in 2019, to seventh in 2020, to completely falling out of the top ten for 2021. Taiwan, the number-two region in 2020, also did not make the top ten in 2021. Korea, Tajikistan and Poland also lost their positions. These countries and regions were replaced by five newcomers: France (0.57%), Germany (0.46%), Norway (0.31%), Croatia (0.28%) and Austria (0.28%).
Conclusion
The year 2021 once again showed a decline in the number of users affected by mobile and PC malware. This looks reassuring, though the risks of infection are far from being gone. Moreover, we have observed another small increase in the share of malware attacks against corporate users versus consumers. The trend of banking Trojans targeting corporate users continued; this is of concern especially if the users working on personal devices are taken into account.
Our research also finds that phishing scammers’ increased focus on e-shops over banks, which began in 2020, is here to stay for the time being as the pandemic effects on consumer behavior persist. These effects include increased online shopping over traditional brick and mortar, an outcome that many economists predict will outlast the pandemic. Cryptocurrency users shall be vigilant, too, for while Bitcoin rates remain high, this is a honey pie for cybercriminals.
For protection against financial threats, Kaspersky recommends that users:
- Install only applications obtained from reliable sources
- Refrain from approving rights or permissions requested by applications without first ensuring they match the application’s feature set
- Never open links or documents included in unexpected and suspicious-looking messages
- Install a trusted security solution, such as Kaspersky Security Cloud, which protects you and your digital infrastructure from a wide range of financial cyberthreats
To protect your business from financial malware, Kaspersky security experts recommend:
- Providing cybersecurity awareness training, especially for employees responsible for accounting, that includes instructions on how to detect phishing pages
- Improving the digital literacy of staff
- Enabling a Default Deny policy for critical user profiles, particularly those in financial departments, which ensures that only legitimate web resources can be accessed
- Installing the latest updates and patches for all software used