Cloud security continues to be a vexing situation, and the tool set continues to become more complex, riddled with acronyms representing possible solutions. Now there’s another: the cloud native application protection platform, or CNAPP. This tool combines the coverage of four separate products:
- A cloud infrastructure entitlements manager (CIEM) that manages overall access controls and risk management tasks
- A cloud workload protection platform (CWPP) that secures code across all kinds of cloud-based repositories and provides runtime protection across the entire development environment and code pipelines
- A cloud access security broker (CASB) that handles authentication and encryption tasks
- A cloud security posture manager (CSPM) that combines threat intelligence and remediation
IT and security managers are looking for a few basic elements from these products, including more accurate threat detection, support for all workloads across multiple cloud deployments, and ways to implement preventable controls.
That is a lot of software to manage, integrate, and understand. However, almost none of the products that claim to be CNAPP have a full set of features that incorporate all four of these categories. What follows is an overview of the landscape and advice on how to navigate amongst the contenders.
Two approaches to CNAPP
There are two ways to approach CNAPP: from the DevSecOps perspective or from traditional IT security practices. The former means more of a focus on protecting the apps themselves (the first two product categories mentioned above), the latter more on expanding traditional network-level protections (the last two product categories mentioned above).
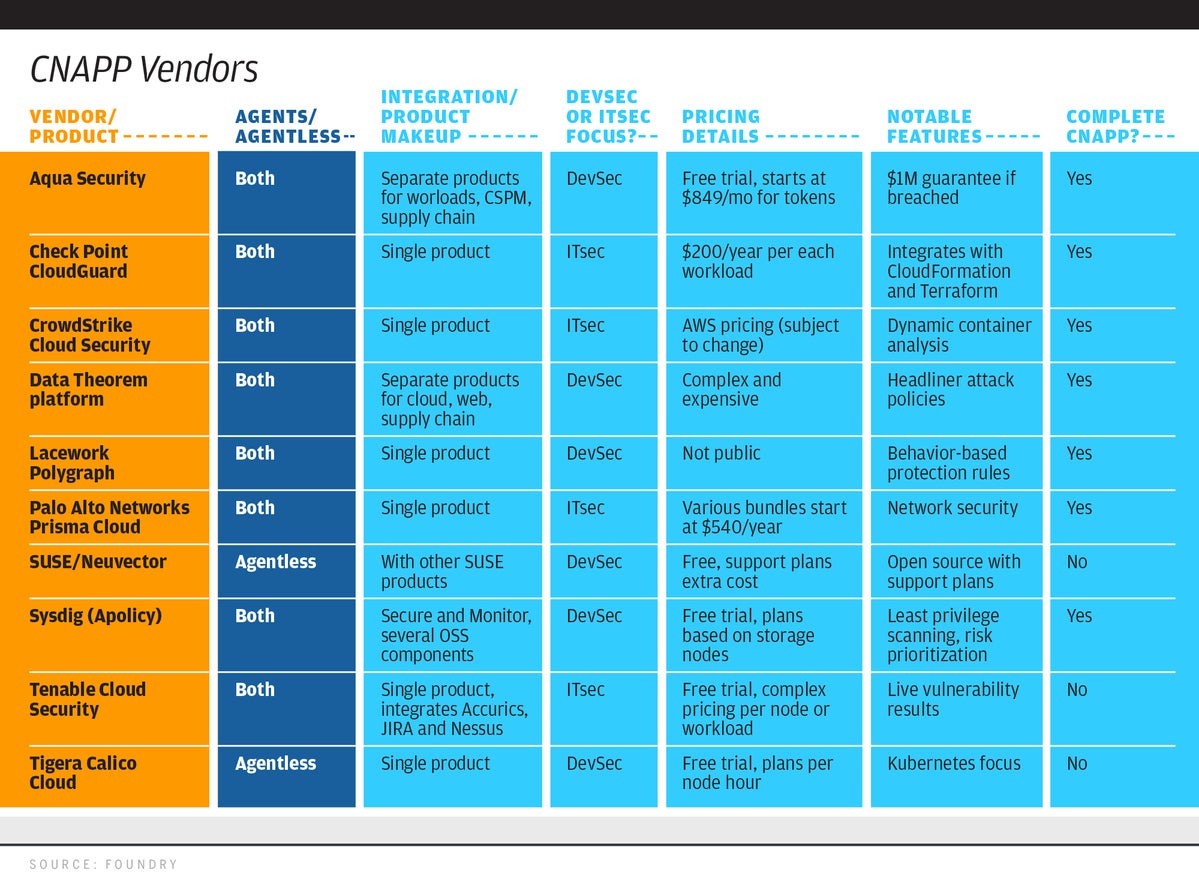
The summary chart below notes which of these two directions each vendor is coming from, other notable and integration features, whether they offer a complete CNAPP solution, and what little information is available about their pricing strategy.
I interviewed the following vendors and summarized the results in the chart below:
- Aqua Security Platform
- Check Point CloudGuard
- CrowdStrike Cloud Security
- Data Theorem
- Lacework Polygraph
- NeuVector/SUSE
- Palo Alto Networks Prisma Cloud
- Sysdig
- Tenable Cloud Security
- Tigera Calico Cloud
The following vendors did not respond to requests for information: jFrog, McAfee, Orca Security, Palo Alto Networks, Qualys, Snyk, Trend Micro, and Wiz.
 Foundry
FoundryWhy CNAPP exists
The key to understanding this product category is all about integration challenges. VMware, in its latest State of Observability report, found that 57% of the respondents claimed up to 50 different technologies are used in a typical cloud app. Organizations typically use many different cloud providers, spreading their risk and moving beyond running their legacy applications across the big three PaaS providers (AWS, Google and Azure) and employing a mixture of private, public and hybrid cloud strategies. This includes various virtual machine instances, Kubernetes containers and using serverless and microservices too.
Organizations will need to control cloud-native application risks, identify weak areas, and remove vulnerabilities. Sysdig in its latest cloud-native security report found that found that 73% of cloud accounts contained exposed Amazon S3 buckets. Is it any mystery that more breaches haven’t happened because of this?
What is working against securing clouds is their success: They have become the de facto computing layer for businesses. “The evolution of cloud workloads and Linux servers into something ubiquitous yet increasingly vulnerable is driving the maturation of the CWPP market,” said Mitchell Hall of Morphisec in a blog post. Part of this maturation is that cloud workloads have many moving parts.
They are also in a state of flux. In Cisco’s latest Hybrid Cloud report, nearly 60% said they are moving workloads between on- and off-premises every week. Some of these apps are running on open-source code repositories and some use in-house code. That is a lot of different use cases to protect.
Speaking of which, Palo Alto Networks’ State of Cloud Native Security 2022 report found that 80% of organizations that primarily use open source security tools have weak or very weak security posture, while the number of enterprises that host more than half of their workloads in the cloud has doubled from 2020. A lot of this growth is coming from the serverless world.
What is motivating this product category can be traced to Gartner, which first used the CNAPP moniker when it issued its “Innovation Insight” report in August 2021. They said that, “Containers and serverless functions are the primary building blocks of cloud-native applications and are becoming increasingly granular with shorter life cycles.” This means that any protection needs to act quickly and unobtrusively. They also found a shift from protecting infrastructure to protecting cloud-based workloads, and the apps that run them. They found many of their corporate clients have stitched together – meaning with little to no automation – ten or more disparate security tools, including dynamic application security testing, web app firewalls, and the four cloud protection platforms mentioned at the start of this post. This one-off, crazy patchwork quilt approach isn’t working.
Ideally, a CNAPP solution should reduce misconfiguration errors, improve security of the development pipeline (commonly called shifting left), and use effective automation. To do that requires having all those acronyms firing on all cylinders. You want to be able to scan for various code elements and vulnerabilities, catch cloud configuration and application coding errors quickly (ideally, when the apps run) and still do the basic security blocking and tackling (like identity and network management). Orca says that “CNAPPs exhibit their real value by intelligently combining data points from different layers in the technology stack to highlight critical security issues instead of just sending thousands of meaningless disconnected alerts.”
Questions to ask when considering CNAPP
Before you try out any of the vendors’ products, think about these questions:
What cloud artifacts can you discover and then regularly scan? Some products (like Lacework) don’t go much beyond the big three IaaS players. Some (like Tigera) just support the Kubernetes services of the big three. Others (like Sysdig) take a deeper dive into containers and the various Linux servers that run them. The real issue is can you continuously monitor all of these artifacts in near real time?
Can you mix agents and agentless across the product’s main dashboard, reports and policies? How are incidents reported? Are there discrete access rules so that various staffers can focus on specific parts of the overall picture? Are there separate or combined pre-built security policies for collecting agent and agentless data? How actionable are your dashboards and its visualizations in showing you the current state of your overall cloud security?
Are all four management tools covered? Some of the vendors, such as Microsoft Defender for Cloud, have CWPP and CSPM elements and you will have to add other components to protect Kubernetes and non-Azure clouds. Tigera comes from the opposite direction, focusing more on containers and their infrastructure.
If you have been involved with infrastructure-as-code to manage your cloud deployments, what devops frameworks are supported (like Terraform, Azure Blueprints, AWS Cloudformation, Demisto)? How does this work with shifting left (in other words, do you scan open-source code repositories)?
Finally, what is the price? Very few vendors are transparent about pricing. Data Theorem takes the prize for the most complex, with different calculations for how many APIs, web and mobile apps, and cloud resources are consumed. Tenable’s is a slight improvement but still complex. Aqua and Tigera have the most transparent pricing. Check Point has the simplest: $200 per year per active workload. Others create synthetic units or bundle various elements that obscure the details.
CNAPP vendors
Aqua Security Platform
Aqua Security has had a series of products (such as for supply chain and workload protection and a CSPM) that it has rolled up into a central hub, too. The company offers a unique $1 million USD guarantee (and FAQ on its specifics here) if a “proven successful attack” happens under its watch. Aqua has transparent pricing, including a free version for smaller installations and plans that start at $849/month for the smallest accounts (using a complex online calculator to estimate your bill). In addition to the big three IaaS, it supports Alibaba, Oracle Cloud, Mirantis, VMware Tanzu, and OpenShift. Multiple levels of workload protection are available, and it supports both agent and agentless methods.
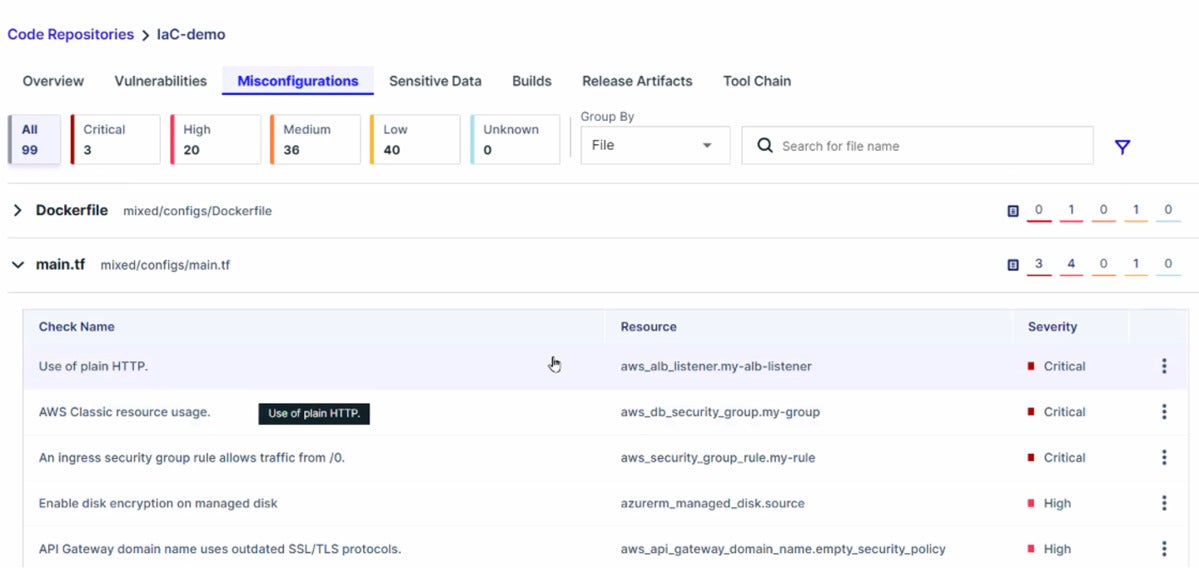 Aqua Security
Aqua SecurityAqua shows the results of its code scan, such as this screen listing various misconfiguration errors.
Check Point CloudGuard
Check Point CloudGuard is a single product, the result of years of combining products from numerous corporate acquisitions such as Dome9 and Protegos. It offers a single dashboard, policy rule set, and support for both agent and agentless methods. CloudGuard integrates with CloudFormation and Terraform and has a simple pricing plan of $200/year USD per each workload. It supports the Alibaba and (soon) Oracle clouds as well as Kubernetes environments.
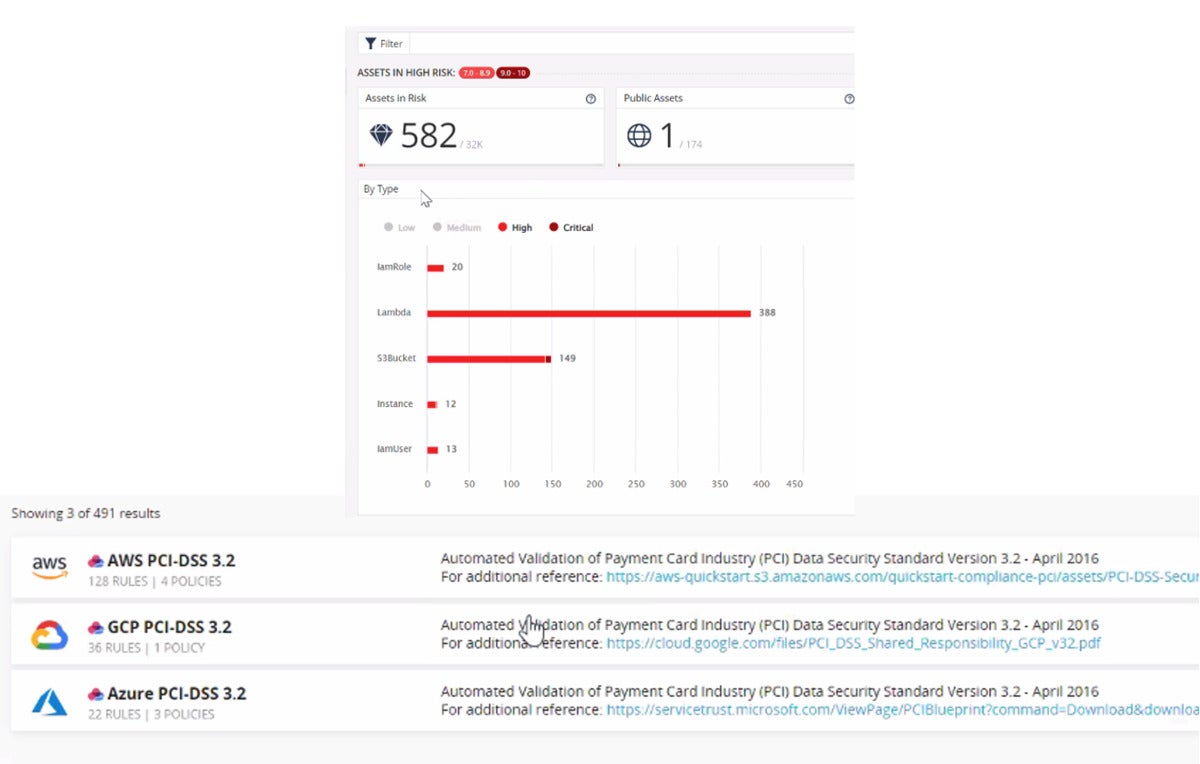 Check Point
Check PointCheck Point Cloudguard shows PCI policies of the big three IaaS platforms and a risk assessment panel.
CrowdStrike Cloud Security
CrowdStrike Cloud Security is packaged as two separate products in its constellation of more than 20 different Falcon protective modules. It has an attractive and unified dashboard that shows you the main incidents and assets of the big three IaaS platforms along with a list of a dozen different container deployments, which are dealt with separately in the dashboard. It covers the CNAPP universe with both agent and agentless methods. It also has an interesting container image vulnerability analysis service.
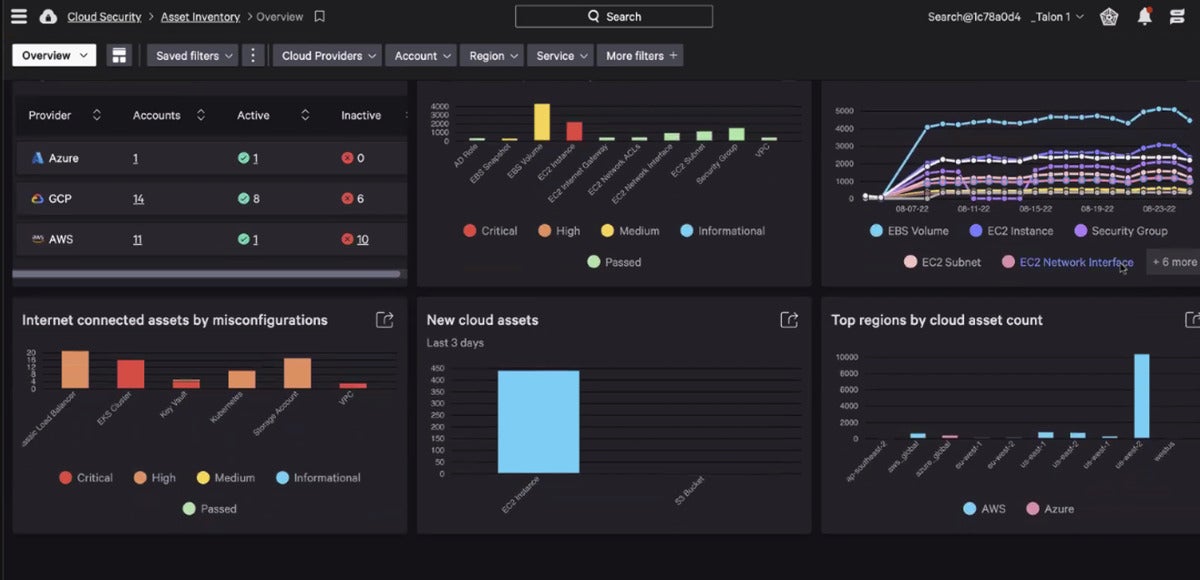 CrowdStrike
CrowdStrikeCrowdStrike’s cloud asset inventory: Containers are assessed in a different collection of menus.
Data Theorem
Data Theorem’s platform covers five separate products that work together to offer CNAPP. These include specialized protection for cloud, mobile, API and web apps as well as a supply chain protection product. It has a central analysis engine and dashboard that provides some integration. Data Theorem supports all the big three IaaS players along with Kubernetes. One notable feature is what it calls “headliner policies” that are constructed to prevent historical breaches. It has both agents and agentless methods. Its pricing structure is complex, with different plans for each product.
 Data Theorem
Data TheoremData Theorem dashboard showing the depth of its various security features
Lacework Polygraph
Lacework Polygraph supports the big three IaaS players along with Kubernetes. It has both agent and agentless methods along with behavior-based detection rules to examine infrastructure as cloud and vulnerabilities. It uses a single, integrated product so policies can span information collected from both methods.
Palo Alto Networks Prisma Cloud
Palo Alto was unable to provide a demo of its Prisma Cloud solution by our deadline, but we decided to include it since it is a market leader. The company built up Prisma Cloud through a series of acquisitions including Redlock (cloud threat defense), Twistlock (container security), and Bridgecrew (developer-oriented cloud security). Palo Alto allows customers to gradually adopt a full CNAPP solution by selling Prisma Cloud on a modular basis or in bundles. Pricing for those bundles starts at $540 USD a year.
SUSE Neuvector
SUSE acquired Neuvector last year and has released its code to open source, making it free to use with paid support plans if needed. It is a partial CNAPP solution, stronger in CWPP and missing CIEM and CASB functionality. It supports all the big three IaaS platforms as well as Rancher, OpenShift, VMware Tanzu and Mirantis container platforms. It is exclusively agentless.
Palo Alto Networks Prisma Cloud
Palo Alto was unable to provide a demo of its Prisma Cloud solution by our deadline, but we decided to include it since it is a market leader. The company built up Prisma Cloud through a series of acquisitions including Redlock (cloud threat defense), Twistlock (container security), and Bridgecrew (developer-oriented cloud security). Palo Alto allows customers to gradually adopt a full CNAPP solution by selling Prisma Cloud on a modular basis or in bundles. Pricing for those bundles starts at $540 USD a year.
 Palo Alto Networks
Palo Alto NetworksPrisma Cloud’s Command Center
Sysdig
Sysdig has two services, aptly named Secure and Monitor, and both are needed to provide CNAPP coverage. Last year the company acquired Apolicy to expand its workload protection features. Besides the big three IaaS players, Sysdig also support IBM, Oracle and VM Tanzu clouds as well as Red Hat OpenShift. It has a pricing page that lacks specifics, but Sysdig told us that plans start at $500/month based on your AWS EC2 storage repositories. Notable features include a new risk prioritization module and the ability to automatically suggest least privilege access rules.
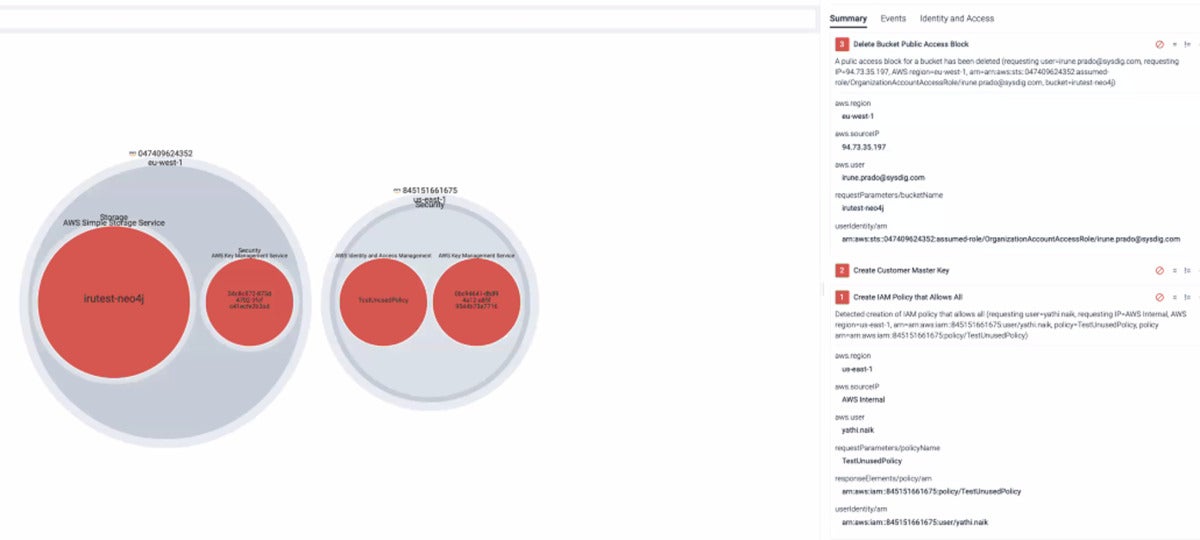 Sysdig
SysdigSysdig’s dashboard shows you the status of its scans.

