- It’s a activity supervisor to allow you to deal with performing safety testing.
- Gives To Do checklists of take a look at circumstances.
- Helps to create bug stories with customization bug templates.
Safety Testing will not be so simple as proper click on > Scan. It is messy, a troublesome sport. What in the event you had missed to check simply that one factor and needed to remorse later? Sh00t is a extremely customizable, clever platform that understands the lifetime of bug hunters and emphasizes on guide safety testing.
Options:
- Dynamic Activity Supervisor to exchange easy editors or activity administration instruments which might be NOT meant for Safety
- Automated, customizable Safety test-cases Guidelines to exchange Evernote, OneNote or different instruments that are NOT meant for Safety
- Handle customized bug templates for various functions and robotically generate bug report
- Help a number of Assessments & Initiatives to logically separate your completely different wants
- Use like a paper – All the pieces’s saved robotically
- Export auto generated bug report into Markdown & submit blindly on HackerOne! (WIP)
- Integration with JIRA, ServiceNow – Coming quickly
- Export bug report into Markdown – Coming quickly
- Customise all the pieces under-the-hood
Set up:
Sh00t requires Python Three and some extra packages. The only approach to arrange Sh00t is utilizing Conda Environments. Nonetheless, Anaconda is non-obligatory when you’ve got Python Three and pip put in – you possibly can leap to step four beneath.
Pre-requisite – One time setup:
- Set up the minimal model of Anaconda: Miniconda and comply with the set up instruction. Keep in mind to reload your bash profile or restart your terminal utility to avail conda command. For home windows, launch Anaconda Immediate and run all of the beneath instructions in that window solely.
- Create a brand new Python Three setting: conda create -n sh00t python=3.6
- Activate sh00t setting: conda activate sh00t. In the event you see an error message like CommandNotFoundError: Your shell has not been correctly configured to make use of ‘conda activate’., you need to manually allow conda command. Comply with the directions proven with the error message. You will have to reload your bash profile or restart your terminal. Attempt activating sh00t once more: conda activate sh00t. Try to be seeing (sh00t) XXXX$ in your terminal.
- Clone or obtain the newest challenge right into a location of your selection: https://github.com/pavanw3b/sh00t. git clone requires set up of Git.
- Navigate to the folder the place sh00t is cloned or downloaded & extracted: cd sh00t. Notice that that is the outer-most sh00t listing in challenge information. Not sh00t/sh00t.
- Set up Sh00t dependency packages: pip set up -r necessities.txt
- Setup database: python handle.py migrate
- Create an Person Account: python handle.py createsuperuser and comply with the UI to create an account.
- Elective however beneficial: Avail 174 Safety Take a look at Circumstances from OWASP Testing Information (OTG) and
- Net Software Hackers Handbook (WAHH): python reset.py.
That is all for the primary time. Comply with the subsequent steps everytime you wish to begin Sh00t.
Beginning Sh00t:
When you’ve got Python Three put in in your machine, you possibly can leap to Step 3.
- For Linux/Mac, Open Terminal. For Home windows, open Anaconda Immediate.
- Activate sh00t setting if not on but: conda activate sh00t
- Navigate to sh00t listing if not in already: cd sh00t
- Begin Sh00t server: python handle.py runserver
- Entry http://127.0.0.1:8000/ in your favourite browser. Login with the consumer credentials created within the one-time setup above.
- Welcome to Sh00t!
- As soon as you’re executed, cease the server: Ctrl + C
- [Optional] Deactivate sh00t setting to proceed along with your different work: conda deactivate.
Improve:
- Navigate to the folder the place sh00t was cloned: cd sh00t
- Cease the server if it is operating: Ctrl + C
- Pull the newest code base through git: git pull or obtain the supply from github and exchange the information.
- Activate sh00t setting if not on but: conda activate sh00t
- Setup any extra dependencies: pip set up -r necessities.txt
- Make the newest database modifications: python handle.py migrate
- Begin the server: python handle.py runserver
Troubleshoot:
Sh00t is written in Python and powered by Django Net Framework. In case you are caught with any errors, Googling on the error message, ought to assist you many of the occasions. In case you are undecided, please file a brand new problem on github.
Glossary:
- Flag: A Flag is a goal that’s sh00ted at. It is a take a look at case that must be examined. Flags are generated robotically based mostly on the testing methodology chosen. The bug would possibly or may not be discovered – however the objective is to intention and sh00t at it. Flag accommodates detailed steps for testing. If the bug is confirmed, then it is referred to as a sh0t.
- Sh0t: Sh0ts are bugs. Usually Sh0t include technical description of the bug, Affected Recordsdata/URLs, Steps To Reproduce and Repair Advice. Many of the contents of Sh0t is one-click generated and solely the dynamic content material like Affected Parameters, Steps needs to be modified. Sh0ts can belong to Evaluation.
- Evaluation: Evaluation is a testing evaluation. It may be an evaluation of an utility, a program – as much as the consumer the way in which needed to handle. It is part of challenge.
- Mission: Mission accommodates assessments. Mission could be a logical separation of what you do. It may be completely different job, bug bounty, as much as you to determine.
Screenshots
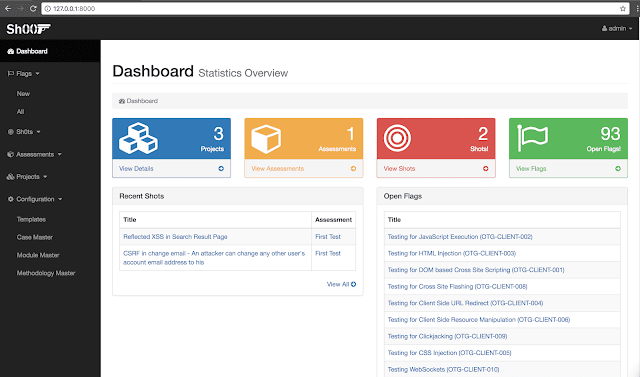
Dashboard:
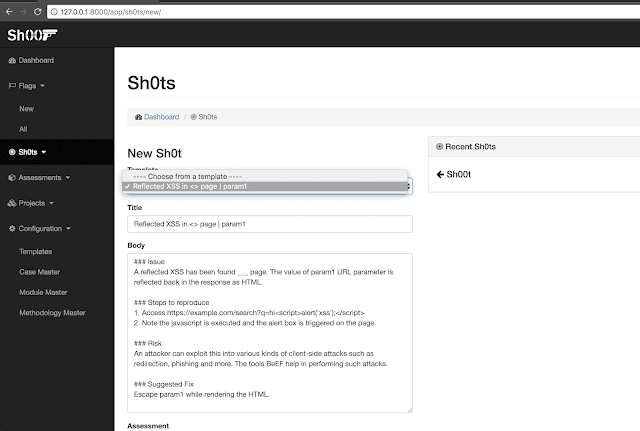
Selecting Methodology and Take a look at Circumstances whereas creating a brand new Evaluation:
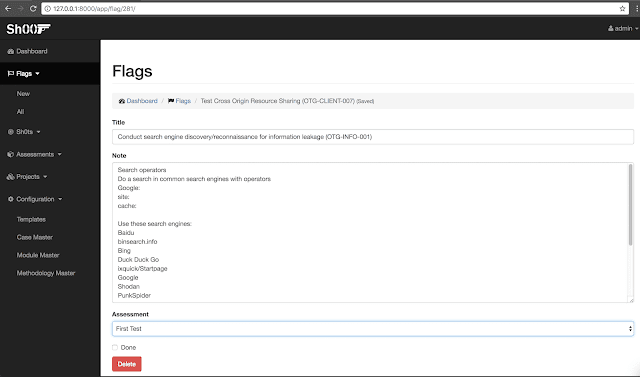
Engaged on Flags:
Submitting a bug pre-filled with a template:
How does it work?
Start with creating a brand new Evaluation. Select what methodology you wish to take a look at with. Immediately there are 330 take a look at circumstances, grouped into 86 Flags, belonging to 13 Modules that are created with regards to “Net Software Hacker’s Handbook” Testing Methodology.
Modules & Flags might be handpicked & personalized. As soon as Assessments are created with the Flags, now the tester has to check them both manually, or semi automated with the assistance of scanners, instruments or nevertheless it is required, mark it “Accomplished” on completion.
Whereas performing evaluation we regularly include customized take a look at circumstances that’s particular to sure state of affairs within the utility. A brand new Flag might be created simply at any level of time.
Every time a Flag is confirmed to be a sound bug, a Sh0t might be created. One can select a bug template that matches greatest, and sh00t will auto fill the bug report based mostly on the template chosen.
Who can use Sh00t?
- Software Safety Engineers: Pentesting & Vulnerability Assessments
- Bug bounty hunters
- Unbiased Safety Researchers
- Blue group, builders who repair
- Anyone who desires to hack
Implementation particulars:
- Language: Python 3
- Framework: Django Net Framework
- Dependencies: Django REST Framework, djnago-tables2: Managed by /necessities.txt
- UI: Bootstrap – Responsive